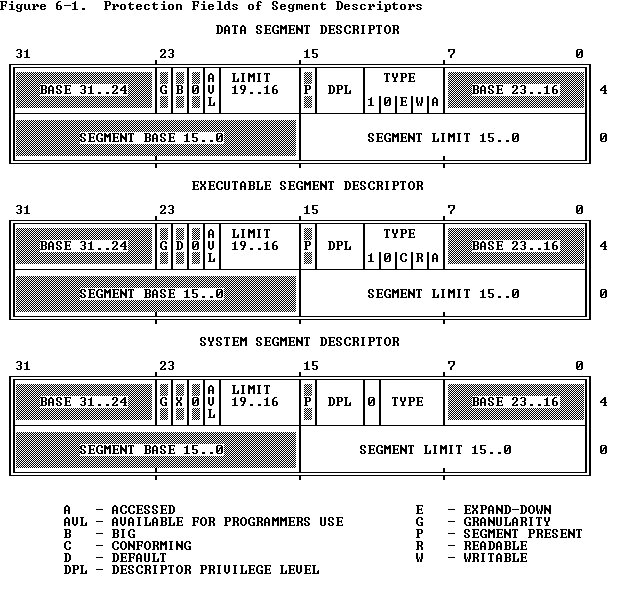
6.3.1.1 Type Checking
The TYPE field of a descriptor has two functions:
- It distinguishes among different descriptor formats.
- It specifies the intended usage of a segment.
Besides the descriptors for data and executable segments commonly used by
applications programs, the 80386 has descriptors for special segments used
by the operating system and for gates. Table 6-1 lists all the types defined
for system segments and gates. Note that not all descriptors define
segments; gate descriptors have a different purpose that is discussed later
in this chapter.
The type fields of data and executable segment descriptors include bits
which further define the purpose of the segment (refer to
Figure 6-1
):
- The writable bit in a data-segment descriptor specifies whether
instructions can write into the segment.
- The readable bit in an executable-segment descriptor specifies
whether instructions are allowed to read from the segment (for example,
to access constants that are stored with instructions). A readable,
executable segment may be read in two ways:
- Via the CS register, by using a CS override prefix.
- By loading a selector of the descriptor into a data-segment register
(DS, ES, FS,or GS).
Type checking can be used to detect programming errors that would attempt
to use segments in ways not intended by the programmer. The processor
examines type information on two kinds of occasions:
- When a selector of a descriptor is loaded into a segment register.
Certain segment registers can contain only certain descriptor types;
for example:
- The CS register can be loaded only with a selector of an executable
segment.
- Selectors of executable segments that are not readable cannot be
loaded into data-segment registers.
- Only selectors of writable data segments can be loaded into SS.
- When an instruction refers (implicitly or explicitly) to a segment
register. Certain segments can be used by instructions only in certain
predefined ways; for example:
- No instruction may write into an executable segment.
- No instruction may write into a data segment if the writable bit is
not set.
- No instruction may read an executable segment unless the readable bit
is set.
Table 6-1. System and Gate Descriptor Types
Code Type of Segment or Gate
0 -reserved
1 Available 286 TSS
2 LDT
3 Busy 286 TSS
4 Call Gate
5 Task Gate
6 286 Interrupt Gate
7 286 Trap Gate
8 -reserved
9 Available 386 TSS
A -reserved
B Busy 386 TSS
C 386 Call Gate
D -reserved
E 386 Interrupt Gate
F 386 Trap Gate
6.3.1.2 Limit Checking
The limit field of a segment descriptor is used by the processor to prevent
programs from addressing outside the segment. The processor's interpretation
of the limit depends on the setting of the G (granularity) bit. For data
segments, the processor's interpretation of the limit depends also on the
E-bit (expansion-direction bit) and the B-bit (big bit) (refer to Table
6-2).
When G=0, the actual limit is the value of the 20-bit limit field as it
appears in the descriptor. In this case, the limit may range from 0 to
0FFFFFH (2^(20) - 1 or 1 megabyte). When G=1, the processor appends 12
low-order one-bits to the value in the limit field. In this case the actual
limit may range from 0FFFH (2^(12) - 1 or 4 kilobytes) to 0FFFFFFFFH(2^(32)
- 1 or 4 gigabytes).
For all types of segments except expand-down data segments, the value of
the limit is one less than the size (expressed in bytes) of the segment. The
processor causes a general-protection exception in any of these cases:
- Attempt to access a memory byte at an address > limit.
- Attempt to access a memory word at an address >= limit.
- Attempt to access a memory doubleword at an address >= (limit-2).
For expand-down data segments, the limit has the same function but is
interpreted differently. In these cases the range of valid addresses is from
limit + 1 to either 64K or 2^(32) - 1 (4 Gbytes) depending on the B-bit. An
expand-down segment has maximum size when the limit is zero.
The expand-down feature makes it possible to expand the size of a stack by
copying it to a larger segment without needing also to update intrastack
pointers.
The limit field of descriptors for descriptor tables is used by the
processor to prevent programs from selecting a table entry outside the
descriptor table. The limit of a descriptor table identifies the last valid
byte of the last descriptor in the table. Since each descriptor is eight
bytes long, the limit value is N * 8 - 1 for a table that can contain up to
N descriptors.
Limit checking catches programming errors such as runaway subscripts and
invalid pointer calculations. Such errors are detected when they occur, so
that identification of the cause is easier. Without limit checking, such
errors could corrupt other modules; the existence of such errors would not
be discovered until later, when the corrupted module behaves incorrectly,
and when identification of the cause is difficult.
Table 6-2. Useful Combinations of E, G, and B Bits
Case: 1 2 3 4
Expansion Direction U U D D
G-bit 0 1 0 1
B-bit X X 0 1
Lower bound is:
0 X X
LIMIT+1 X
shl(LIMIT,12,1)+1 X
Upper bound is:
LIMIT X
shl(LIMIT,12,1) X
64K-1 X
4G-1 X
Max seg size is:
64K X
64K-1 X
4G-4K X
4G X
Min seg size is:
0 X X
4K X X
shl (X, 12, 1) = shift X left by 12 bits inserting one-bits on the right
6.3.1.3 Privilege Levels
The concept of privilege is implemented by assigning a value from zero to
three to key objects recognized by the processor. This value is called the
privilege level. The value zero represents the greatest privilege, the
value three represents the least privilege. The following
processor-recognized objects contain privilege levels:
- Descriptors contain a field called the descriptor privilege level
(DPL).
- Selectors contain a field called the requestor's privilege level
(RPL). The RPL is intended to represent the privilege level of
the procedure that originates a selector.
- An internal processor register records the current privilege level
(CPL). Normally the CPL is equal to the DPL of the segment that
the processor is currently executing. CPL changes as control is
transferred to segments with differing DPLs.
The processor automatically evaluates the right of a procedure to access
another segment by comparing the CPL to one or more other privilege levels.
The evaluation is performed at the time the selector of a descriptor is
loaded into a segment register. The criteria used for evaluating access to
data differs from that for evaluating transfers of control to executable
segments; therefore, the two types of access are considered separately in
the following sections.
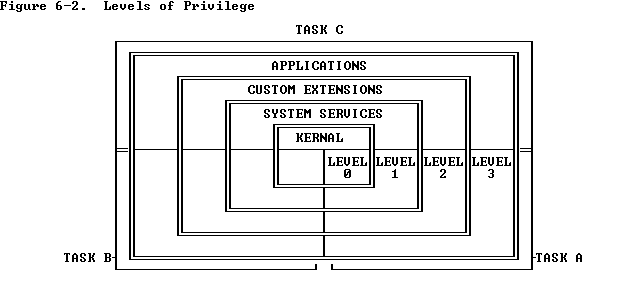
Figure 6-2
shows how these levels of privilege can be interpreted as rings
of protection. The center is for the segments containing the most critical
software, usually the kernel of the operating system. Outer rings are for
the segments of less critical software.
It is not necessary to use all four privilege levels. Existing software
that was designed to use only one or two levels of privilege can simply
ignore the other levels offered by the 80386. A one-level system should use
privilege level zero; a two-level system should use privilege levels zero
and three.
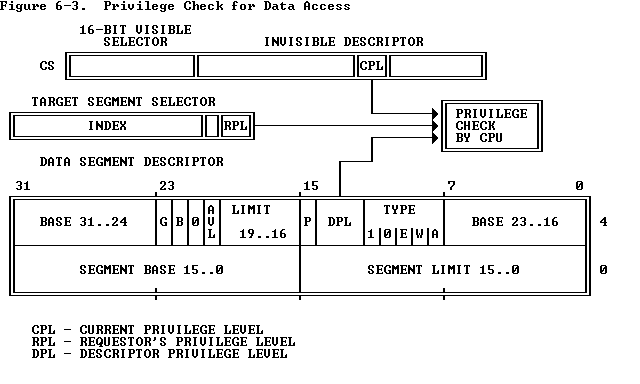
6.3.2 Restricting Access to Data
To address operands in memory, an 80386 program must load the selector of a
data segment into a data-segment register (DS, ES, FS, GS, SS). The
processor automatically evaluates access to a data segment by comparing
privilege levels. The evaluation is performed at the time a selector for the
descriptor of the target segment is loaded into the data-segment register.
As
Figure 6-3
shows, three different privilege levels enter into this type
of privilege check:
- The CPL (current privilege level).
- The RPL (requestor's privilege level) of the selector used to specify
the target segment.
- The DPL of the descriptor of the target segment.
Instructions may load a data-segment register (and subsequently use the
target segment) only if the DPL of the target segment is numerically greater
than or equal to the maximum of the CPL and the selector's RPL. In other
words, a procedure can only access data that is at the same or less
privileged level.
The addressable domain of a task varies as CPL changes. When CPL is zero,
data segments at all privilege levels are accessible; when CPL is one, only
data segments at privilege levels one through three are accessible; when CPL
is three, only data segments at privilege level three are accessible. This
property of the 80386 can be used, for example, to prevent applications
procedures from reading or changing tables of the operating system.
6.3.2.1 Accessing Data in Code Segments
Less common than the use of data segments is the use of code segments to
store data. Code segments may legitimately hold constants; it is not
possible to write to a segment described as a code segment. The following
methods of accessing data in code segments are possible:
- Load a data-segment register with a selector of a nonconforming,
readable, executable segment.
- Load a data-segment register with a selector of a conforming,
readable, executable segment.
- Use a CS override prefix to read a readable, executable segment whose
selector is already loaded in the CS register.
The same rules as for access to data segments apply to case 1. Case 2 is
always valid because the privilege level of a segment whose conforming bit
is set is effectively the same as CPL regardless of its DPL. Case 3 always
valid because the DPL of the code segment in CS is, by definition, equal to
CPL.
6.3.3 Restricting Control Transfers
With the 80386, control transfers are accomplished by the instructions
JMP,
CALL,
RET,
INT, and IRET,
as well as by the exception and interrupt
mechanisms . Exceptions and interrupts are special cases that
Chapter 9
covers. This chapter discusses only JMP,
CALL, and RET instructions.
The "near" forms of JMP, CALL, and
RET transfer within the current code
segment, and therefore are subject only to limit checking. The processor
ensures that the destination of the JMP,
CALL, or
RET instruction does not
exceed the limit of the current executable segment. This limit is cached in
the CS register; therefore, protection checks for near transfers require no
extra clock cycles.
The operands of the "far" forms of
JMP and
CALL refer to other segments;
therefore, the processor performs privilege checking. There are two ways a
JMP or
CALL can refer to another segment:
- The operand selects the descriptor of another executable segment.
- The operand selects a call gate descriptor. This gated form of
transfer is discussed in a later section on call gates.
As
